Mortar And Tile Adhesive Hpmc,Tile Adhesive,Waterproof Mortar Flexible,Mortar Ceramic Tile Adhesive Jinzhou City Tujin Building Materials Co.,Ltd. , https://www.hpmctujin.com
How to ensure the security of the Internet of Things? Solution and next steps
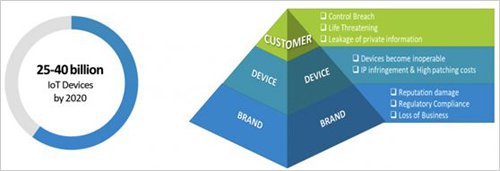
A recent HP study found that about 90% of devices are collecting some form of personal information. This means that user privacy is always at risk and the level of threats will grow with the development of the Internet of Things (IoT). As people's security awareness increases, security solutions are now being adopted, but identifying vulnerabilities in common deployment architectures remains a key issue. Companies have begun to consider not only protecting their IoT ecosystem, but also protecting their users. This model means that businesses can ensure end-to-end security of user data and open up new revenue streams by providing IoT security as a service.
The impact and challenges of IoT security
In recent years, attacks against the Internet of Things ecosystem have grown exponentially. Malware, such as Mirai, has proven that access to millions of devices can be granted through the device's default username, password, or simple dictionary attack. As smart home devices send more than 600,000 malicious spam and hackers remotely hijack cars, any connected device is vulnerable.
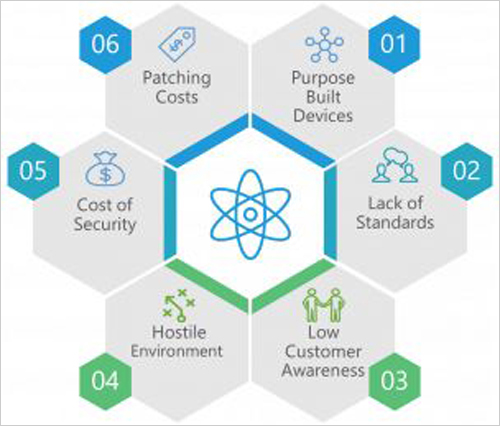
The challenges facing the IoT ecosystem are very different from traditional IT. It’s probably not enough to just understand the technology of the attack. You should understand the scope, purpose, and motivation of using these specialized devices to disrupt the entire network. These devices have limited computing power and therefore cannot always run powerful protection mechanisms such as antivirus, two-factor authentication, and key certificate exchange. These factors make it easier to target users when attacking. Because most end users lack security awareness, they don't apply strong passwords and don't fix device vulnerabilities often. Businesses do not necessarily regularly investigate devices that maintain password policies and firmware updates deployed on their customer networks, opening up the entire network for bad participants.
Since IoT devices are usually built specifically, universal security standards are difficult to develop and have not yet been adopted internationally. Unlike typical IT endpoints (such as laptops, desktops, and tablets), IoT devices are deployed unsupervised in a remote environment, which means they are also susceptible to physical tampering.
While intrinsic security seems to be the best way to solve security problems, it can cause devices to use the same protocol for many years without updates, and it also increases deployment costs because the cost of "safe" chips is $7. Between $17. Since the average cost of the device itself is $10, the inherent security can greatly increase the overall cost.
Opportunity to use IoT security
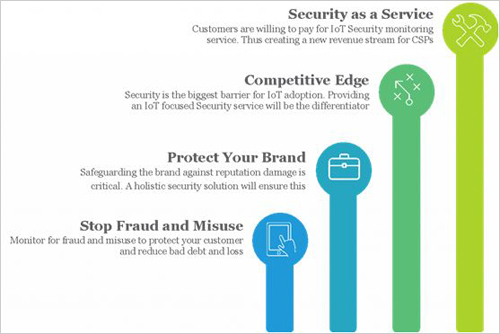
Traditionally, operators have provided Internet of Things connectivity to tablets in a vertical channel. But with the introduction of IoT and M2M technologies, various device types, models, and variants have been introduced into the network, most of which are constrained and prevent security agents from running internally. The best way to protect these devices is to cover agentless, unknowable protection to monitor the ingress and egress traffic of these devices.
CSPs are able to monitor the behavior of the devices they provide to these devices because traffic to and from these devices flows through their network. This gives telecommunications companies an opportunity not only to allow connectivity, but also to provide their users with basic security services as value-added services, or to implement IoT security productization in one of the following ways.
Why do organizations need a secure Internet of Things?
The amount of information generated from endpoints and exchanged between the IoT and IT networks continues to grow, but there are no substantive standards to follow in the IoT deployment. While many organizations are working together to build new technologies and standards, it may take several years for the industry to adopt or accept these standards. Since millions of data nodes are generated outside the organization's network, these information, data channels, and endpoints should be handled with the importance they deserve.
The size of the Internet of Things and the number of under-protected endpoints are much larger than any traditional IT network, so the security risks are much higher. Considering that IoT devices have been deployed in vital sectors such as healthcare, banking and emergency services, their security cannot be underestimated.
(This article was compiled from the Internet of Things space station: Securing the IoT: Problems, Solutions, and Next Steps)